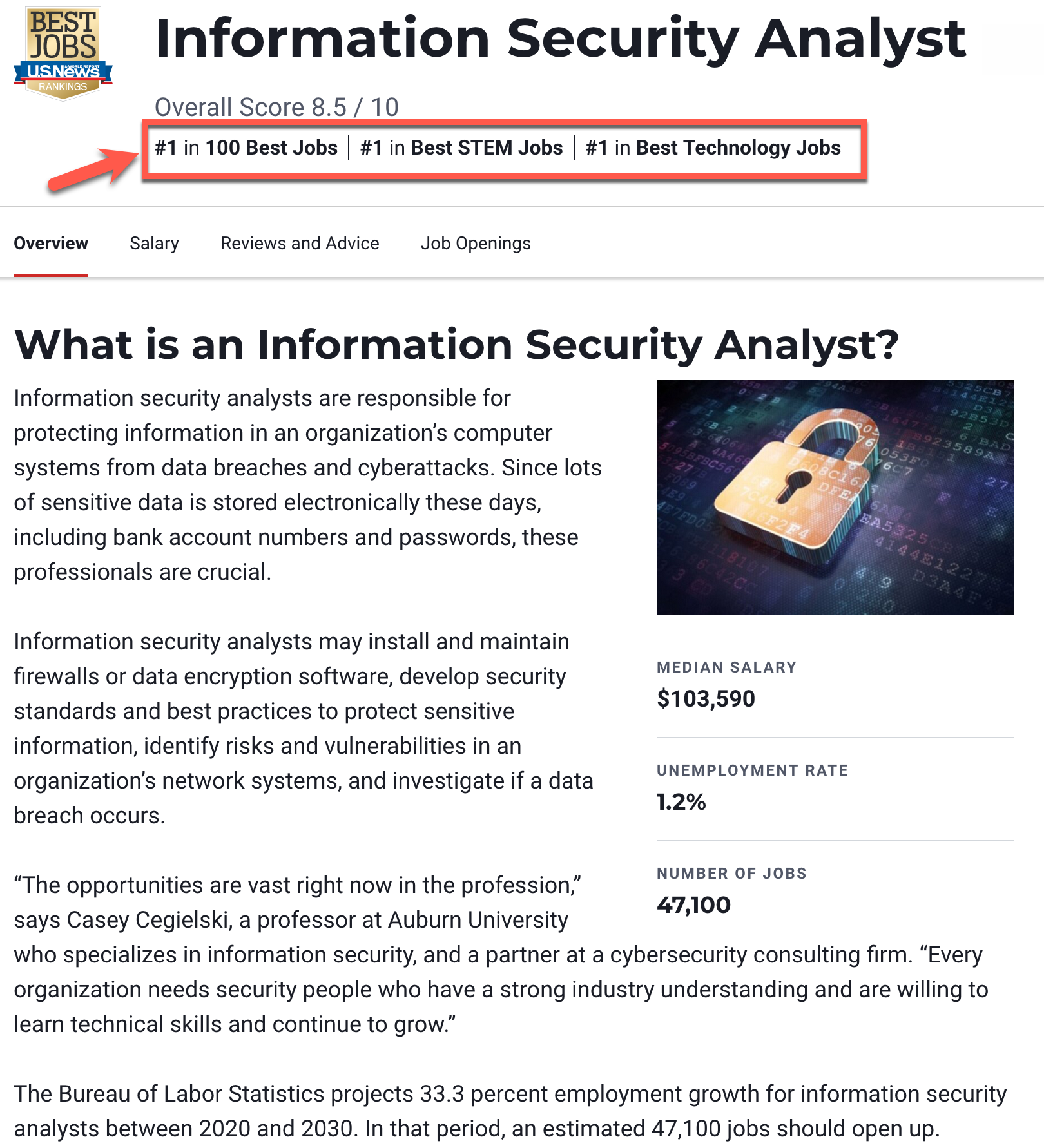
Here's a story I'm incredibly happy to be able kick off this blog with: US News & World Report has named Information Security Analyst jobs as:
- The #1 spot in Best STEM Jobs
- The #1 spot in Best Technology Jobs, and ....
- #1 in Best Jobs!
How awesome is that?! Check it out for yourself: https://money.usnews.com/careers/best-jobs/information-security-analyst
If you know me, you know this is a job near and dear to my heart. As someone who has done the job for years, managed a team of analysts, and now teach and consult on, it's great to see some positive press for the role! What I'd like to do in this article is lend some additional perspective as to why I think being a cyber security analyst is one of the most awesome careers you can have right now. I'll also address some of the most common complaints or worries you might have if you're thinking about taking a cyber security analyst role. Let's break it down...
First - What is a Cyber Security Analyst Job?
If you haven't done the job before and are curious what it actually entails, here's a quick breakdown. For those who already know, go ahead and skip to the next section.
"Cyber security analyst" (a role also commonly named "SOC analyst", "information security analyst", "cyber security engineer", and more) is a role that can mean slightly different things at different organizations. But speaking in generalities here, this is the job that involves you watching corporate endpoint, network, and cloud activity for signs of a cyberattack, and then taking action to stop it. You can image it sort of as being the immune system for an organization's IT infrastructure. In practice, this will involve:
- Security tool setup and monitoring - Choosing, setting up, and monitoring the output of security tools such as intrusion detection systems, EDR (or XDR) tools (which function sort of like a black box for an endpoint, recording all activity in case of compromise), a SIEM, packet capture, and more.
- Detection Engineering - Writing the rules to implement on your security tools to catch attacks in progress. This involves both knowing which rules to write
- Threat Intelligence - Not so much producing it yourself (that's what threat intelligence analysts do), but knowing where to find it, how to apply it, and what intelligence is the most relevant to you and what will help you build the best customized defense for your org.
- Threat Hunting - Your tools cannot and will not catch everything. Therefore, you have to go out and proactively look at all the benign-seeming data you've captured and give it a double check, looking for anomalies that might indicate attackers have found a way in that avoided all your security tools
- Triage and Investigation - Ask any SOC analyst, on any given day there are likely multiple alerts that are wanting your attention. Therefore, your job as an analyst involves not only getting through them all, but getting through them in a logical prioritized order. This means looking at a bunch of potential problems with partial data and doing your best to read between the lines and understand which alerts must take priority and which can wait. Once you jump into any given alert, you also must balance time pressure with quality investigation and figure out if you have a true problem, or if it was a false positive alert.
- Response - When something goes wrong, security analysts are often on the hook to solve the problem! This means both stopping the attack and figuring out what happened. Stopping the attack requires understanding your tools and network and isolating infected systems, cleaning them up, and returning them to normal operation. It also means collecting forensic evidence from your security tools and even the endpoint or cloud service itself, reconstructing the attack to understand if the breach was successful or stopped early enough to prevent disaster.
- Malware Investigation - If your investigation found that malware was installed on the system, it will be hard to know what happened if you can't figure out what that malware does, how it communicates, and what files it writes/changes/drops to take control of a system. Discovering if a breach was successful or not often comes down to something like "This malware sample uses a HTTPS protocol backdoor to domain examplebadsite[.]com, our proxy log and packet captures show traffic to that domain, including command and control activity, bidirectional file transfers including sensitive data, and more, indicating we were successfully breached!" While malware analysis can be a skill on the more advanced side, it's also in my opinion, one of the most fun parts of the job.
Not all SOCs or security analysts do all these things, some organizations with larger security teams will break things down into specialized roles, so if you're considering one of these jobs, ask which parts of detection and response the team does, and which it does NOT do. My guidance here is the more things you do, the better. As they say, "variety is the spice of life." There's some research out there to show that variety in security analyst roles is one key way to steer clear of burnout from doing the same repetitive activity too often!
Why I Think SOC Analyst Jobs Are Awesome
Thought I could go on all day about this, from my perspective, here are the top 3 reasons I think working in a SOC is awesome.
#1 The Job is a Challenge (In the Best Kind of Way)
Are you a person that likes a good puzzle? A challenge? Are you a problem solver that likes to see results from your solutions? If so, cyber security analyst is an awesome job for you! Believe me when I say you will be facing a new problem every day. A new adversary attacking your network, a new malware sample was found, a new vulnerability just dropped that you have to figure out how to detect, the list goes on and on.
Security is what Simon Sinek would call an "infinite game", and each day you have to balance the needs of the now vs. the longer term and broader needs of your organization. Security jobs are NOT just "turn on every security feature and lock everything down 100%". Newcomers to the job are often surprised by that, but remember, our organizations don't exist to be secure, they exist to produce something of value, and hope to be as secure as possible while doing it. For you, the analyst, this means balancing risks that must be taken to get productive work done with the best protection you can offer, given the tools you have. The overarching goal from our perspective? Make sure that cybersecurity problems are minimized, and ideally cyber security issues are never the reason your organization grinds to a halt or sustains such a large monetary hit that it threatens the organizations existence. Ultimately if you can keep cybersecurity problems off the list of things executives need to worry about, and any damage that is done is under an acceptable threshold (no it doesn't have to be "perfect security, zero damage"), you're succeeding as a cyber security team in my book! How do you achieve that? Well, that's the fun challenge in being a security analyst, you get to figure it out every day!
#2 The Job Outlook is Amazing (and Getting Better)
Given the press this article started with I probably don't need to sell this part to you, but here's my take. We all want a job we know isn't going anywhere anytime soon. Can anyone imagine a world where cyber security isn't relevant for at least the lifetime of everyone reading this article? I can't. Everything is getting connected to the internet, generating data, and moving to the cloud, and all that needs to be secured and monitored.
Beyond the need for the job though, what else makes the outlook amazing? Well other big factors in any career choice are whether they are satisfying and fun to do (covered in part 1) and pay a livable wage. Security jobs in general pay very well. How well? Here's info from the ISC2 Global Information Security Workforce study from 2021 on all cybersecurity professionals.

Here's the info from Glassdoor.com on cyber security analysts specifically (note the page for Sr. Cyber security analyst is even better, but they split that out into different numbers.) This data appears to roughly agree with the ISC2 survey above.
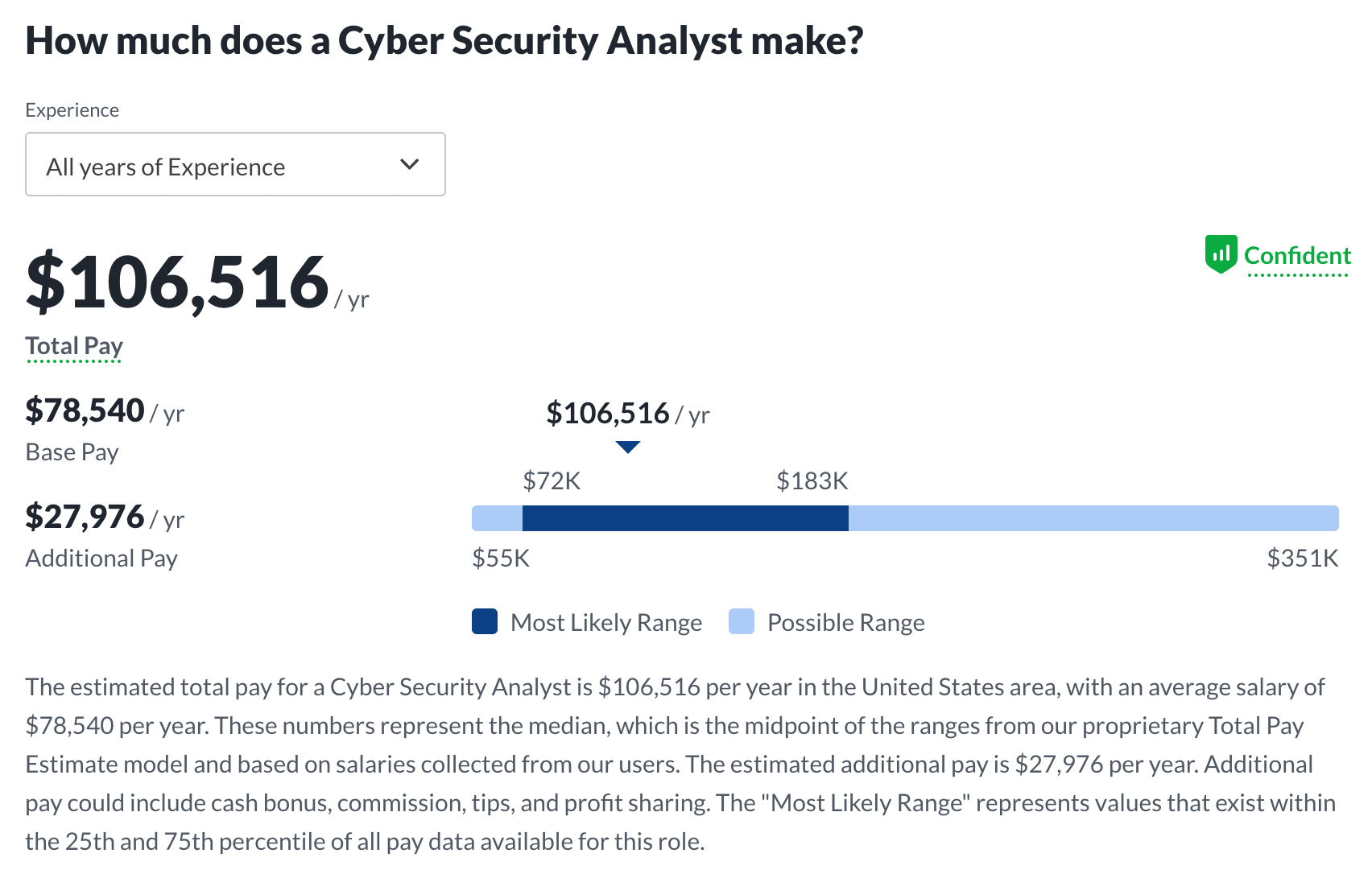
That's way above average for the US at least, so no arguing on the salary front that cyber security analyst jobs are awesome!
Side Note: Is Automation Making Cyber Analyst Jobs Obsolete?
While tools and methods for securing our networks are undoubtedly improving in major ways compared to just a few years ago, we are nowhere near "security is solved". While defenders have made things better, attackers continue to raise the bar as well, and with the advent of cryptocurrency and ransomware attacks, everyone is trying to get a slice of the pie. Cyber defense is as relevant as ever, if not more so, and I see no signs this trend won't continue. According to Sophos a ridiculously high 66% of businesses surveyed were effected by ransomware in previous year, which was a 78% increase compared to the previous year, yikes! 90% of those attacks affected the organization's ability to operate, and the average payment was $812k!! We need your help cyber defenders!
"But I heard automation is going to make security analysts obsolete!" No way, not yet at least. It certainly is making the job easier and eliminating some of the boring or repetitive parts of the work and perhaps significantly changing what cyber analysts will do at their job, but it sure isn't getting rid of us any time soon! These tools in my experience are more a supplement to help humans figure things out more quickly and accurately, but nowhere near a replacement for a human brain.
#3 The Security Industry is Awesome
Look, I've never been a lawyer, or an accountant, or a doctor so I could be wrong here, but I can't imagine any of those professions have conferences and a community that is anywhere near as fun as security meetups and conferences. Do you have any friends that can say something like "my job just sent me to a conference where I got to physically disassemble and hack at a voting machine and check it for vulnerabilities?" I doubt it. But I can!
- Here's a picture of me doing exactly that at the DEF CON voting village in 2019 (with defintely the coolest shadow I've ever had in a photo).
- Here's another pic of me going at a table full of consumer electronics at the IOT village a few years before that.

Want to check the security cars, planes, boats, IOT devices, industrial control systems and more? DEF CON (and other conferences) has that as well! Want to learn how to pick locks? Get a RFID chip implanted in your hand so you can unlock doors without a key? Learn and watch social engineering attacks in action? It's all there. What about meeting people with world-class knowledge on specific products and areas of technology? They're all there at security conferences and in my experience very approachable and willing to share. I love going out to security conferences and jumping around from village to talk to workshop and trying to take in everything I can, it's a great way to spend a few days and keep your skills sharp! In short, I think this industry does a great job of throwing fun events that contribute to continuing education in a way that makes you actually want to go to them, I don't have many friends from other industries that would say that about their conferences.
Perhaps this final section sounds like a promotion for the security industry as a whole, but as someone in a cyber security analyst role, being the best at your job requires knowing the leading-edge research and the art of the possible. Going to security conferences is one of the best ways of getting that information and staying on top of the latest research and trends, and it's a boat load of fun given the incredibly awesome people who work in security, not just another stuffy work conference (notice I'm not wearing suit in the pic above, security cons are generally very casual and laid back). If you've never made it out to one of the major conferences like BlackHat or DEF CON, you owe it to yourself to go, but don't forget about the equally awesome smaller regional conferences and even localized ones like Security BSides. If you're thinking about a security job, attending these kinds of events is a great way to start to learn what you're getting yourself into, they are beginner friendly so don't be afraid to buy a BSides ticket and go hang out for a weekend somewhere!
Conclusions
If you're considering jumping into a SOC job, hopefully this article helps convince you that being a security analyst is
- A fun, and challenging, but ultimately very rewarding career
- A job role that isn't going anywhere and will certainly allow you to pay the bills
- Something the world needs a LOT more of right now!
You may read that SOC analyst jobs are dull/boring/repetitive/a steppingstone to something better. While certainly some aspects of that do exist in certain roles, that's something I believe is more job and organization specific than it is inherent to the work itself. As I mentioned, cyber defense analyst roles are something that I've done myself for years without running into these problems, and I meet plenty of students who agree. If you're in a SOC role that isn't as fun, don't despair, I'm going to write another article on how to make SOC jobs awesome in the future but for now, this intro article has gone on long enough. If you've made it this far, thanks for reading!
If you're interested getting pushed a notification any time I write a new article, hit the subscribe button below.
If you're interested in cyber security analyst training to take through work, check out my week long super in-depth SOC-related courses at available through the SANS institute. For staying sharp day to day, check out my YouTube channel and the Blueprint podcast for SOC and security analyst relevant tips and tricks. All are linked on my SOC Training resources page.

