Dear LastPass,
Writing this is tough, but unfortunately, you've given me no choice but to leave you and delete my account. In this post, I'm going to lay out in detail why that is, and what I would've expected from a first-rate security company in a situation like yours. It won't be fun, but it's important for you and every other password management company to hear.
First, let me start by saying I’ve been a paying customer for over a decade. I've got the receipts:
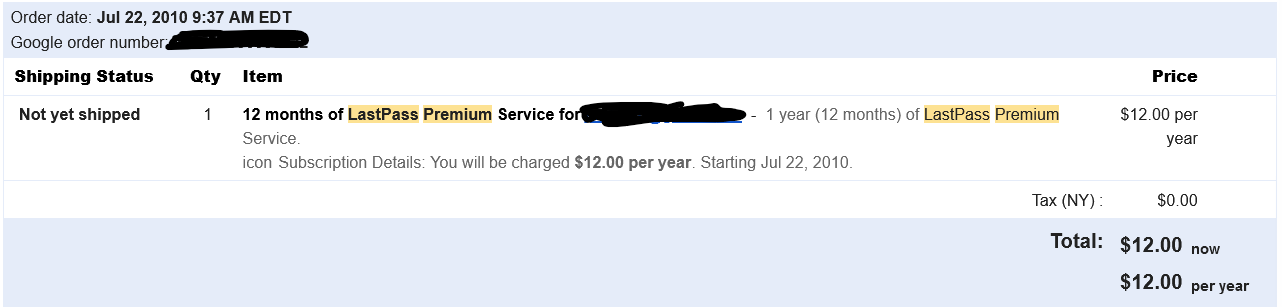
Ever since I joined as a premium member in 2010, most things have been great. You’ve enabled the random, long, and unique password lifestyle and saved me untold inconvenience from having to worry about a single breach growing from password reuse, and for that, I thank you. Sure, you’ve made some mistakes along the way, but I felt those were adequately and transparently addressed to the point of satisfaction, and perhaps even building my trust in you. I even asked some colleagues about this, and they all felt the same way. Those well-handled situations lead to my continued use of your service.
This time, it’s different. As a security professional and cyber defense instructor who has recommended your service numerous times to students, friends, and family over the years, I now wish I hadn't. The way you've handled this breach makes it clear that you are unfortunately no longer a company we can trust with our most important data (and maybe haven't been for a while, though we didn't yet know it). As a result, I'm making the painful decision to delete my account and move to another service. Not only that, but I'll also be shifting from recommending you, to warning others about your mistakes in hopes that something like this will never happen again to those trying to find a trustworthy password management solution.
This is not out of spite, but more so trying to gain something positive from the negative. It's a teachable moment for others on how things can go wrong, and a chance for learning, so we won't repeat the problems of the past. Therefore, I'm writing this "open letter" style post to spell out to readers item by item, what it would've taken to handle this situation in a way that would've kept me, and likely many other customers as well.
It's All About Trust
This post will not be a rant about the absurdity of losing the password vaults of all your customers. I'm sure you know exactly the magnitude of that mistake. While that's a big enough problem to drive many away, your encryption scheme does indeed take some of the worry off the table for those who used a long complex password. The issue that this post focuses on, and why I'm leaving as a customer, is much bigger and more important to your future as a business, and that issue is trust.
Simply put, trust is everything for you, your single most valuable asset. If your customers cannot 100% trust everything you say and do, they simply will not let you guard their most trusted secrets. As the saying goes, "trust takes years to build, and seconds to break." I'm sure you know this, but somewhere over the years you must've forgotten. It is now apparent that you aren't currently capable of making trust-building decisions and have been slipping in the past as well. Here is the list of those decisions from my perspective as a customer.
Before the Breach
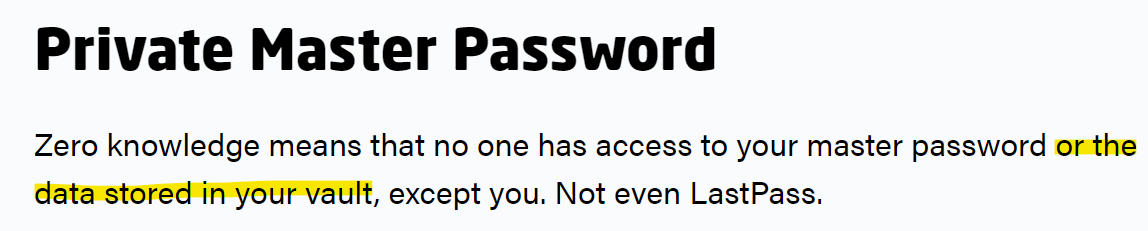
My first example is creating marketing buzz terms like "Zero Knowledge security models" that you had to have known were false, or at best, only partially true to the point of being clearly deceiving. You should've known when you typed those words that you'd be in trouble someday when the inevitable happened, but I guess that didn't worry you, and now here we are. Specifically, you told us that you had no access to sensitive information on the data in our vault. Two examples. One from the LastPass website (emphasis/highlights in the below quotes added by me):
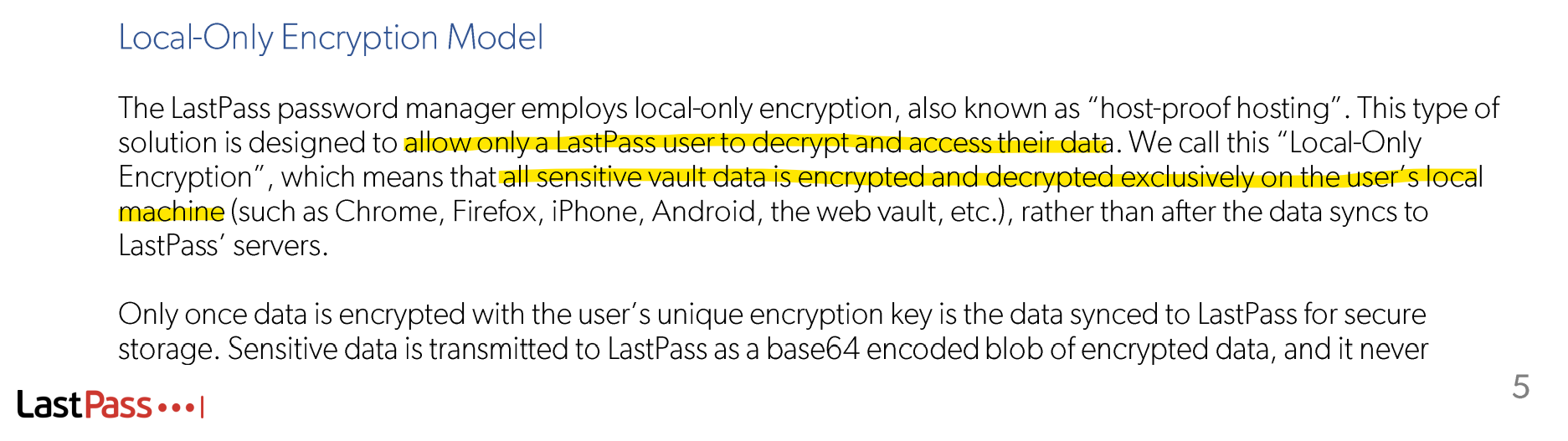
The second being your technical paper, which says effectively the exact the same thing.
Only once data is encrypted with the user's unique encryption key is the data synced to LastPass for secure storage. Sensitive data is transmitted to LastPass as a base64 encoded blog of encrypted data, and it never touches LastPass servers in a way that can be visible to LastPass.
Given your verbiage here, I, and many others, interpreted that as "My vault, and everything I see when I decrypt it is encrypted in its entirety in an opaque blob that you store for us". We now know that apparently what you meant is "some things are visible, some are not", given your breach statement.
"...stored in a proprietary binary format that contains both unencrypted data, such as website URLs..."
This lie still exists on your site right now, actively misleading your customers! Why did that claim even get made in the first place? Worse, why are you still making a demonstrably false promise about your product? That alone is absolutely ridiculous and throws everything else you say into question. That, to me, is unforgivable in a product space like password storage and management and would be enough to steer me away before I joined, had I known it.
Sure, URLs are not the most sensitive part of the data, but I'm not interested in partial and deceptive truths from a password storage company. What this looks like from a customer perspective is that your standards had already unacceptably slid pre-breach, and that's just the mistake you made before the breach.
LastPass Vault Breach Response and Communication
This is the really big one in my mind. While we have no idea how the technical parts of the incident response went, that almost doesn't matter to us, because you really screwed up the communication. In a situation like this the importance of full detail and fast communication cannot possibly be understated here. This is my #1 complaint about this whole scenario. You must have known what you were doing, and why it wasn't good enough, and if you honestly didn't know, that's just as big of a problem.
In the past I’ve felt fairly good about both your timeliness in communication and the quality of info provided during other security incidents. The transparency felt good and seemed like you were leaning towards over communicating, building my trust in you. But this time it was different. That transparency wasn't there, nor was the timeliness of communication or enough detail to help me solve the problem you created for me. Without a fumbled, delayed, and misleading response, honestly, you probably would have kept me as a customer but unfortunately that's not the path you chose. Instead, you gave a partial explanation of the breach that seemed avoidant of details that would be embarrassing for you. You didn't help me understand my specific risk level. And then, to make it worse, it appears you tried to bury the lead by announcing it just before Christmas. That plan wasn't smart, it actually added to the stress of having to clean up your mess instead of being with my family, and that just made me extra angry and wary that it would happen again in the future. That should’ve been an obvious outcome to you as well.
I don't want to only throw stones here. I want to give detailed constructive criticism of what could've bene done better, so let's discuss in more detail how I would've preferred you to handle this.
What LastPass Should Have Done
As a customer of your service (or really any password manager), here's what I think would've been appropriately expected under a vault breach scenario:
Timely Notification of the Incident
For something this important, this should be obvious: I want to know right away! I assume some PR person may have coached you to announce the vault breach at a time where people wouldn't notice, but in my mind, this backfired in two ways. One is that telling me there's a problem right before trying to go on vacation means I can no longer do that. Instead, I had to rush to change passwords and clean up your mess or risk my own security. Did I need to do that? Maybe or maybe not, your lack of detail made it unclear to me, and I had to take the approach of better safe than sorry. That just makes me angrier and doesn't make anything better for either of us.
The second and more important item is that it makes me think you didn't tell us extremely important information as soon as you had it, which no matter the season, is the #1 thing I need from a service like yours. Instead of trying to save your customers with a timely notification, you (unsuccessfully) tried to prioritize your own reputation instead of our security. This was one of the worst offenses in my mind. Perhaps you truly did make that discovery on December 23rd, but you sure didn't make any attempt at explaining that. That means your customers have to assume you knew, and just sat on that crucial information. That's unacceptable when our sensitive information is on the line.
Give Us a Date the Breach Occurred
For the love of God, tell us when the data was stolen! You didn't include the day the passwords vaults were accessed, making it impossible for me to know how to scope the breach. Are you kidding me? That is an absurd detail to leave out. Not including a piece of data that is so obviously important for risk remediation is embarrassing for you. Did the vault access happen in August? December? That's a big difference in how many passwords may need to be changed for some people, especially people that joined your service during that time and loaded all their passwords into it. Honestly, I have no idea why you wouldn't include that information. This shows either a lack of understanding, a lack of care, or that you are still trying to hide something, none of which is acceptable.
A Warning About Old Accounts Having Lower PBKDF2 Rounds
Below is a pic of your announcement, attempting to calm people because of how many rounds of PBKDF2 you apply. However, you really avoided one highly important detail, and that is that some accounts were/are not protected at the normal level of security - the oldest ones.
Again, this is another inexplicable and irredeemable move on your part. I stayed with your service for over a decade and effectively got punished for it. A breach is not the time to hide customer-endangering details, but it sure seems like that's what you did here:
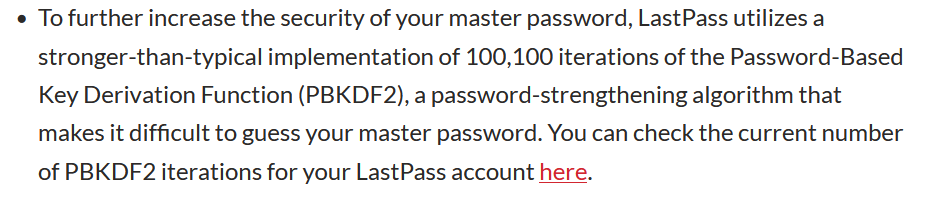
What else would I have expected here? It's quite simple. Add "if you have an account made before x date, then you may not have the standard number of PBKDF2 rounds applied leading to additional and potentially significant risk exposure". How hard is that? You also could've given those with a lower number a separate email, actively letting them know this. This shows that you couldn't take the simplest of measures to ensure your most loyal customers were protected. Who would want to stay with a service like that? More thoughts on PBKDF2 to come.
A Clear List of What Was Breached
Again, from the breach notification:
...that contains both unencrypted data, such as website URLs, as well as fully-encrypted sensitive fields such as website usernames and passwords, secure notes, and form-filled data.
Unencrypted fields "such as...", encrypted fields "such as...". Are you kidding me? Which ones were and were not encrypted? We need to know in exact specificity. Your incredibly vague list of items is not clear enough for something this important. A common example question I saw in the online discussions: Were all of the notes stored in each site’s entry encrypted, or just my “secure notes”?
You might know what you meant, but if you look around the internet and on the Reddit discussions on this, customers don't understand, and that's the standard you have to hit. When customers have to work together to reverse engineer and decode your cryptic messages, that's not a good look, nor is it a vote of confidence for you protecting our data. (Side note: LastPass users, check that link for a more detailed breakdown of the exposure.) Us figuring it out ourselves is a clear signal your communication attempts have failed, and LastPass should've immediately clarified, whether you thought it was needed or not. The fact that others had to both do the work to figure it out, and other customers had to rely on them for the information is absolutely ridiculous.
I would not be that worried about my data that was stolen if it was encrypted. However, I'm not 100% sure of what all was encrypted and what wasn't, beyond the minimally stated info and what others have discovered. Not giving us the info we need leaves me frustrated and confused on what I need to worry about (changing passwords and reviewing URLs on Christmas Eve), and also makes you look like you’re hiding something. Hiding and being deceiving or incomplete in a breach communication means you've lost me. Again, it’s all about trust.
Acknowledge That You Lied and Correct Your Marketing Materials
Flat out, I believe LastPass intentionally lied to us, I see no other reasonable conclusion here. Again, quote your own breach notification.
...contains both unencrypted data, such as website URLs, as well as fully-encrypted sensitive fields such as website usernames and passwords, secure notes, and form-filled data.
"Unencrypted data"...

"Unencrypted data"...
Sensitive data is transmitted to LastPass as a base64 encoded blog of encrypted data, and it never touches LastPass servers in a way that can be visible to LastPass.
"Unencrypted data"...
You get the point.
This is you clearly lying to your customers at worst, and an intentional weaseling of terms at best. LastPass - in hopefully no unclear terms, this is absolutely unacceptable on your part. You've lied about one of the most important aspects of the core of why you exist. I wouldn't be surprised if class-action lawsuits show up for this one. Are you intentionally lying to us? Or do you not understand that URLs are a sensitive field and also failing (intentionally or unintentionally) to tell us what is considered our "vault" and what isn't? Again, inexcusable for something this important.
Perhaps you would counter this by saying that URLs are not part of what you would consider my "vault". Well then where does it say that? It doesn't. You're clearly trying to lead people to believe that every bit of information you store related to our vault is encrypted, and it's not. That's just completely unacceptable from a security company that stores critical data.
LastPass, you need to acknowledge your lie or incompetence, explain it, and apologize for betraying your customers' trust and misrepresenting your product. And for the love of God, change the "Zero Knowledge" copy on your website. You are not “Zero Knowledge,” you had lots of unencrypted data while both claiming that you didn’t, and also not telling us what is included in that and what is not in enough clear detail to assess our risk. This is also a huge part of why I will not be using your service anymore. Fool me once, shame on you, fool me twice, shame on me. There won't be a second chance for you here.
Note to readers: If you use another password management service, it's at this point you should question whether they are giving you the same lies or not, and how you can verify that. "Trust but verify" right? This problem is not easily fixed by just moving to another password manager that simply says they do it right. We should be looking for verifiable proof.
A Way to Assess My Specific Risk
Why did I have to go out and find my own sources on how long it would theoretically take to crack a password at the length and complexity I use? As a user, I want you to provide a tool or chart, with a way to enter my password character length/complexity and how many rounds of PBKDF2 were applied on my account and get back a ballpark time estimate of how safe I am against modern password attacks. Would all people use or understand that tool? Maybe not, but many would, considering your tech savvy user base. You know that not every user used a strong, long master password, and also doesn't have 100,100 rounds of PBKDF2, so we needed to know this information. It could be a link for those who are interested in deep diving details if you're worried about it cluttering your core communication. The risk presented to a person with a 10-character master password with a very old account and only 1 round of PBKDF2 vs a new account with 100,100 rounds and a 24+ character password is very different. Again, not delivering what we need to protect ourselves.
A Specific Preemptive or Retroactive Low PBKDF2 Round Count Warning
Speaking of PBKDF2 rounds again. Let me back to that, again quote from your own breach announcement:
"We routinely test the latest password cracking technologies against our algorithms to keep pace with and improve upon our cryptographic controls."
As soon as the announcement was made, I immediately thought about all the rounds of PBKDF2 theoretically applied to my vault. Fortunately, I was one of the likely small subset of users that was aware of that feature and the ability to control it, though I admittedly hadn't revisited it in quite a while. Considering that and my extra-long password I thought “I should be OK, right?” since 100,100 rounds would indeed make it absurdly slow to try to brute force guess my password. I still wanted to verify, so I immediately logged in to check how many rounds of PBKDF2 were applied to my account.
Guess what I found? To reward my long-time premium member status, I actually found that I was well below the 100,100 PBKDF2 rounds that are now standard. My vault was set around 20k instead. Why? Because even though in the past I had manually upped the number above the normal at the time. That round count continued to need to grow as technology improved and I hadn't gone back and done it again. Foolish me? To some extent yes, I can take some blame for that. But also, I am not a cryptography expert, so I also had no idea what a “good” number is. I also didn't know I needed to since LastPass never warned me or encouraged me to do so, which is the thing I believe they should've done. Why was there no audit for low-round accounts with a warning to keep up? This sure doesn't feel like helping me "keep pace with and improve upon cryptographic controls", another reason you've lost my trust.
Sure, I could’ve looked it up and changed it and didn’t. That part is partially my fault, but I also had no reason to believe I needed to, thinking I had outsourced that work to you based on your promise to protect my data. Your customers are paying you to protect them on factors that they aren't an expert on assessing. I think it's fair to expect that you tell us when our account is below a new standard for security and either automatically upgrade us to a better standard (preferable), or at least email me or give me a popup on login telling me that standards and password cracking tech have changed to the point where I need to improve the PBKDF2 number to remain secure. What I also would've liked here was a notification after the breach saying "we noticed your account was less than our standard during the breach" so that I was aware of that and didn't have to go digging in advanced options to find it. I understand upgrading PBKDF2 round count is a minor disruption to end users since you have to re-encrypt and re-download your vault on all devices, but I think most people would be happy to do it. Instead of being able to make that decision for myself though, you, as a security product company, decided that convenience was more important than security for me. Again, in my book, that is an unforgivable failure on your part, and a breach of trust and failure to perform a basic duty of the service.
A Warning of What Users Might Expect Now
For readers, let me make this clear again: LastPass storage is not "Zero Knowledge", it's "partial knowledge" and we now know that due to this breach. That's a very important difference considering that unencrypted, breached data "such as URLs" can both be sensitive in their own right just by exposing what sites and services someone uses, but also may contain sensitive parameters such as links to reset passwords, auth token material, or links that should be hidden from public knowledge.
To the first point, think of just some of the most obvious scenarios - those working against oppressive regimes, whistleblowers, human rights work, undercover work, or anything where you need to stay confidential and maintain some kind of OPSEC. This is just the beginning. In my opinion, LastPass should be helping users understand why the data that was confirmed leaked unencrypted could be used against them, and how they might prepare for that. Leaking the list of sites a customer has saved is indisputably sensitive by any reasonable definition. Many of them might not matter - Facebook, YouTube, Gmail, etc., but a certain few may be very significant. If you disagree, please publicly post your email address and the list of all sites in your own vault and see what else happens once the internet gets a hold of it.
Users of your service now have to consider, and potentially expect that their identities could be compromised mapping their email addresses to their potentially anonymous usernames and more, and that all of their accounts on all sites might be more easily compromised given a better profile of their internet activity. This also increases risk of targeted spear-phishing scenarios for victims from whoever stole the data, especially if they end up releasing it to the public someday. That would be a true nightmare. Why did you not mention this? Cause you didn't care? Cause you don't want to bring it up? Cause you assume it's too complex for customers to understand? Sorry, none of those are acceptable reasons in my book. You need to mention the impact of the data you leaked.
Conclusion
This is not an open letter post just to let out my frustration. The core goal here is to share how, even in a situation like this, an organization can preemptively and post-breach, manage to keep customers and retain as much trust as possible. Unfortunately, LastPass has become the newest case study on how to fail at this. Hopefully security professionals and anyone else reading this can keep the points in mind and sway their own org from fumbling in these ways in future breach situations. If you recognize any of these issues in your own product, service, or otherwise, please take this as a warning to fix them before it's too late!
Here is what it comes down to:
- LastPass betrayed their user’s trust in multiple ways
- Their marketing contains falsehoods on the security of their product, and they still have it posted even after we know it's false, a double whammy
- They appear to have tried to prioritize their reputation over user security by announcing details just before a common vacation time
- Their communication details post-breach were infuriatingly lacking in detail, and also tried to avoid stating important information on how to recover, what your specific risk was, and what to expect as a result
It hurts me to have to write all this about a company that I was so positive about for so long, but the errors and omissions here are egregious to such a degree that a knowledgeable person can only walk away from this feeling betrayed, lied to, and that their data is not in safe in your hands. You have lost our trust. You are likely going to lose your most security savvy customers, and ruined your reputation, and that worst part is that so much of that was unnecessary. The stink of this incident is going to follow you in the enterprise security crowd, hurting future business, and for that you only have yourself to blame.
Next time, if you get a chance, do better. Your customers deserve it.
